Command your attack surface
A unified view of assets across your entire digital estate.
Make shadow IT and poor security posture a thing of the past by monitoring your internal and external asset inventory to spot coverage gaps and areas lacking security controls.

Proactively harden your defenses by leveraging native and third-party enrichment to understand the exposures adversaries are most likely to exploit.
With relevant context around assets and exposures, teams can respond faster and triage the full blast radius of an attack.
Surface Command: Key capabilities
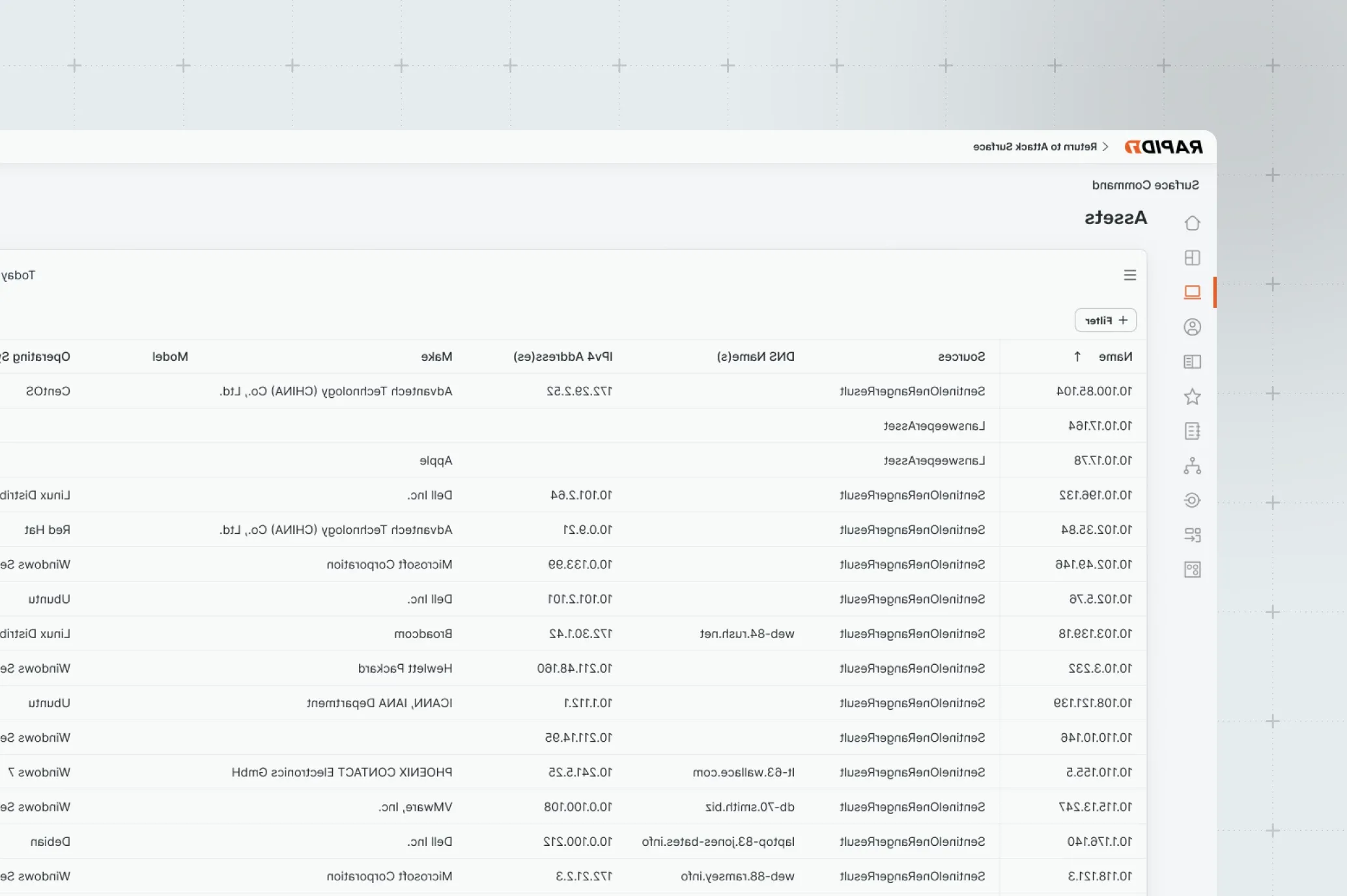
Eradicate blind spots
Continuous discovery helps you protect both internal and external assets: Eliminate security blind spots and quickly uncover exposed assets so you can harden your attack surface and put a stop to frequent attacker exploitation.
Defend with full context
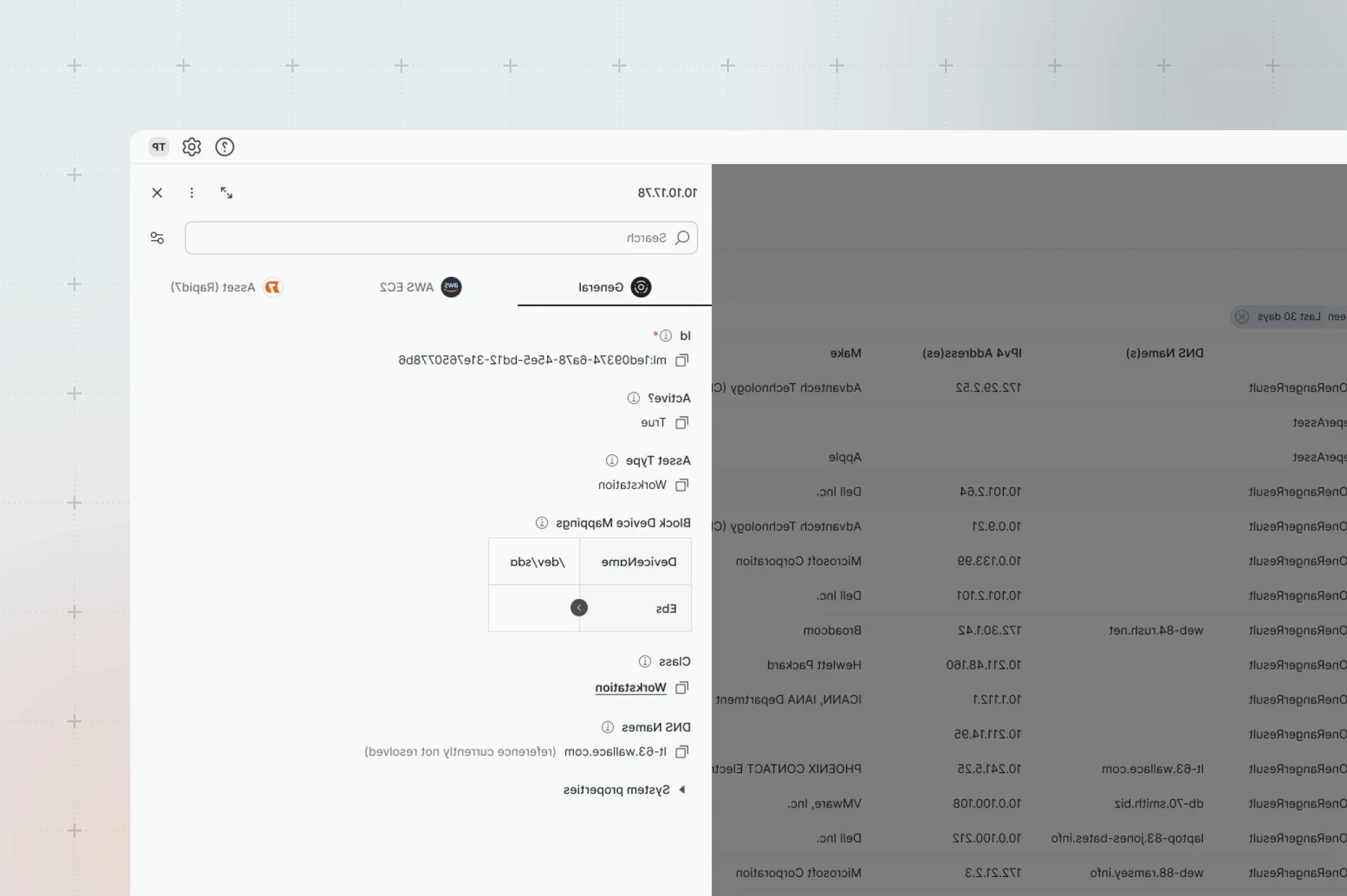
Native and third-party enrichment combine to provide critical business context so you can smash security-data silos, see which exposures pose the greatest risks, and prioritize remediation accordingly. Save more time and automate the protection of strategic business units.
Accelerate response
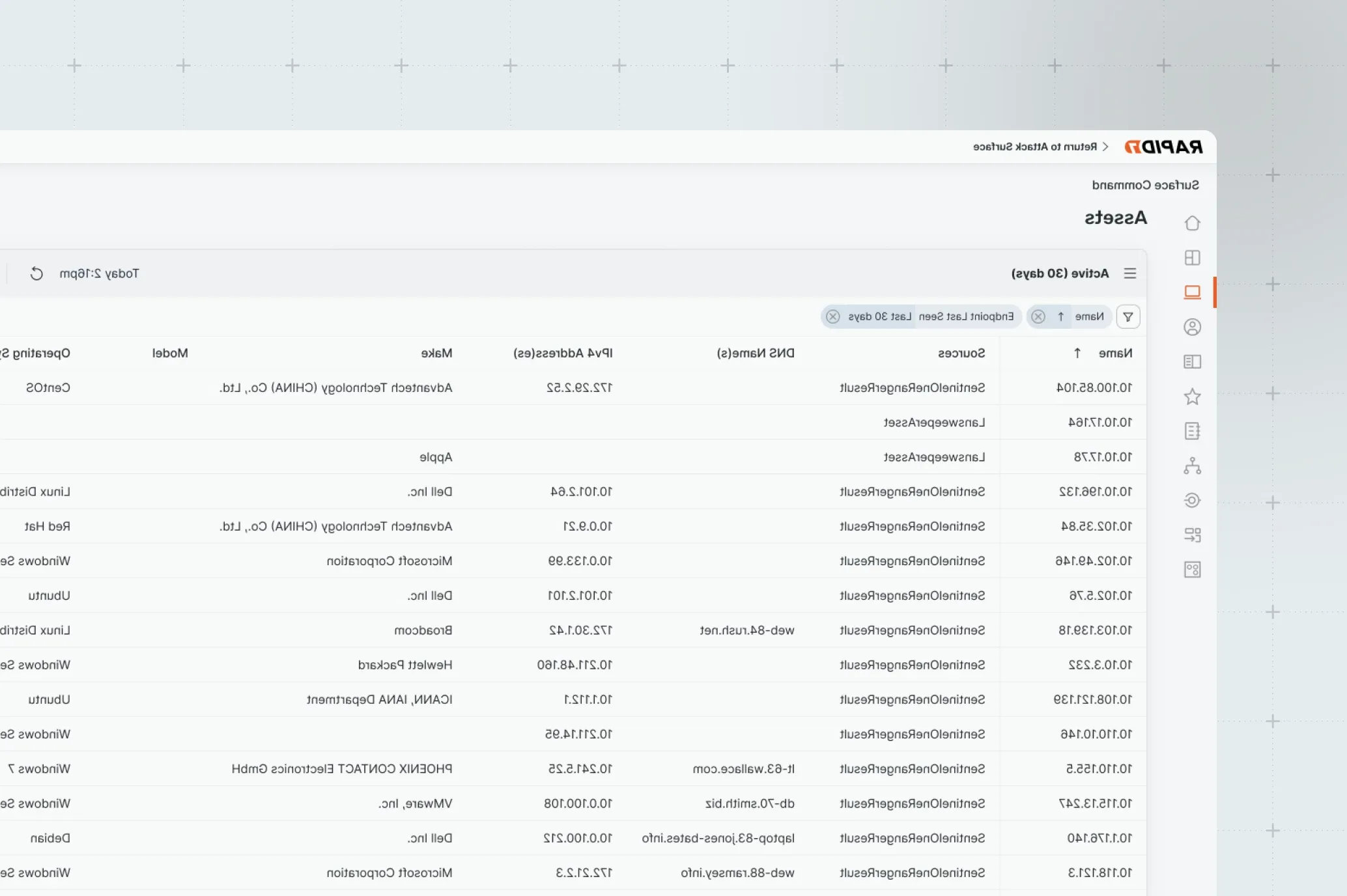
When threat actors start exploiting attack paths, security teams are already too late in their response and likely must manually triage the situation. Increased context enables more proactive measures due to an improved perspective into potential access points through which attack paths are created.
Get started here
Compare tiers and capabilities.
Surface
Command
A continuous 360° attack surface view teams can trust to detect and prioritize security issues from endpoint to cloud.
Exposure
Command
Attack surface visibility with proactive exposure mitigation and remediation prioritization across your hybrid environment. Eliminate high priority exposures with threat-aware risk context.
Exposure Command
ADVANCED
Stronger security for your workloads leveraging real-time visibility, identity analysis, and automated remediation. Code-to-cloud protection also includes continuous web-app scanning and expanded risk coverage for modern, cloud-native environments.

